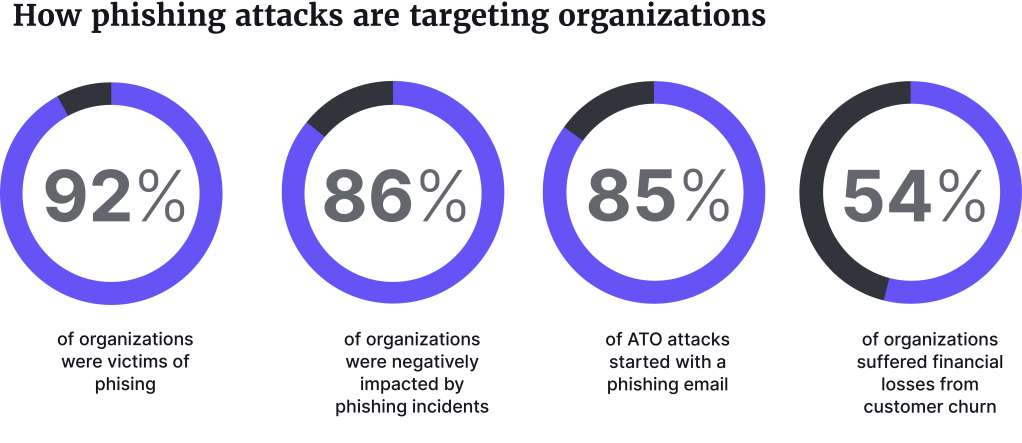
Phishing attacks continue to be one of the biggest security threats as cybercriminals improve their tactics. A staggering 92% of organizations say that they have been victims of successful phishing attacks in the last year, according to a new Email security risks report 2023 from Egress.
A majority (91%), say they have experienced outbound email data loss in the last 12 months, 86% report negative impacts of email incidents, and 85% experienced account takeover (ATO) attacks after being phished.
“Even harder for traditional technology to detect are text-based attacks that rely on social engineering and attacks launched from trusted compromised supply chain email addresses. It’s not just these technologies that struggle to detect them – people do too.”
Jack Chapman, VP of Threat Intelligence
Almost half of the phishing emails (44%) were classed as ‘technical’ – meaning that they were specifically designed to bypass signature-based defenses.
Social engineering
The top three ‘most successful’ types of phishing attacks that organizations fell victim to were:
- phishing involving malicious URL or malware attachment;
- supply chain compromise; and
- social engineering.
Egress noted that social engineering was present in 39% of the attacks, which pressure recipients to engage. “Without advanced anti-phishing technology that uses natural language processing (NLP) it is virtually impossible for organizations to detect text-based social engineering attacks”, the report states.
The most common impact of the attacks was customer churn, where about half, (54%), said that they ended up losing customers and revenue due to the attack. Just under half, 47%, said that their reputation was damaged.
Social engineering attacks
Social engineering is the term for malicious activities accomplished through human interactions. Cybercriminals use psychological manipulation to trick people into making security mistakes or giving away sensitive information.
One common example of social engineering is to target new employees who might be less aware of the organization’s processes, or impersonation of brands or leaders within the organization.
Phising risk
Egress sees a concerning trend in the growing sophistication of phishing emails. Attackers are getting more refined tools and methods, and more attacks are automated.
“Malicious payloads are tried and tested – and cybercriminals will stick to an attack for as long as it works. While attackers might stick to the same type of payload (URLs and attachments), they will evolve the actual payloads. This combination of proven results and attack evolution means phishing risk continually remains high,” said Jack Chapman, VP of Threat Intelligence.
“Even harder for traditional technology to detect are text-based attacks that rely on social engineering and attacks launched from trusted compromised supply chain email addresses. It’s not just these technologies that struggle to detect them – people do too.”
Malicious payload
A payload is the part of the attack which causes harm to the victim, and can sit harmlessly for some time until it’s triggered.
Fear of AI
As phishing attacks are getting more sophisticated, almost every organization in the report (99%) mentions stress about email security. Another rising risk factor is the use of AI, with 72% of cybersecurity leaders said to be concerned about its use within phishing emails.
“There’s potential for AI-powered chatbots to rapidly produce an increased volume of highly convincing phishing emails and for deep fake technology to add video and voice capabilities that can be used in combination with text-based phishing and as part of vishing attacks”, the report states.
Vishing attacks
Vishing attacks are a type of social engineering attack performed over the phone. Fraudsters use psychology to trick victims into handing over sensitive information or perform some action on the attacker’s behalf.
Security awareness and training
Even with the high number of attacks, almost all (98%), said that they carry out security awareness and training (SA&T). Most organizations carry out training monthly (39%), 29% weekly and 13% fortnightly. Financial firms said that they were 10% more likely to perform weekly practises than monthly.
“There’s potential for AI-powered chatbots to rapidly produce an increased volume of highly convincing phishing emails and for deep fake technology to add video and voice capabilities that can be used in combination with text-based phishing and as part of vishing attacks.”
Egress Email security risks report 2023
Still, more can be done as 96% voice a concern with their SA&T programs. Over half (59%) said that “there was an element of box-ticking to it” and do the training for compliance purposes. And 46% felt that employees aren’t engaging enough with training, and are just “skipping through as quickly as possible”.
“People need real-time teachable moments that engage them at the point of risk to tangibly reduce the number of security incidents that occur and augment SA&T,” said Jack Chapman.


