A hacker group named Medusa is threatening to leak thousands of stolen documents from a private clinic Sofiahemmet in Stockholm unless they are paid $1m within the next few days.
The hackers say they have stolen 60,000 documents, and have announced their intention to sell the information to whoever pays first.
The attack was discovered on February 27, and started when all the phones were knocked out. The private clinic said that it quickly turned off all computers, and could carry out planned care work thanks to earlier set safety routines.
It said in a statement that it has not found any signs of patient data or other sensitive data being stolen in the attack. But an intensive investigation is underway with IT experts and the Swedish police.
The Medusa ransomware group appeared in late 2022, and is known for targeting multiple industries such as high technology, education, manufacturing, healthcare, and retail.
According to IT security specialist Karl Emil Nikka, Medusa “doesn’t care” whom it attacks, which makes the group stand out because many hackers avoid attacking hospitals because of the potential for actual harm to patients.
Attacking government websites
Multiple attacks on various Swedish organizations have been carried out this year, with cyber actors linked to Russia involved. This could well be a response to Sweden joining the North Atlantic Treaty Organization (NATO). Former Prime Minister Magdalena Andersson warned about the possibility of such attacks in 2022 when her party decided to seek NATO membership.
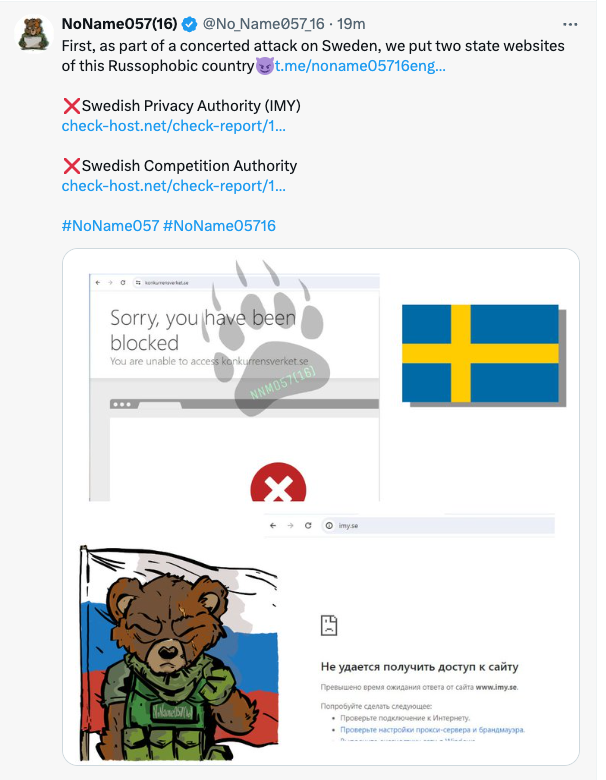
On March 5, the pro-Russian hackergroup NoName057 took credit for carrying out overflow attacks which successfully shut down two government websites, including Integrationsmyndigheten (the Swedish Authority for Privacy Protection) and Konkurrensverket (Swedish Competition Authority).
No data has been stolen or compromised in these two attacks.
The group announced the ‘successful attacks’ on Telegram and X, and added that more on “Russophobes” should be expected.
“Russian hackers have teamed up again and this time decided to bring down Sweden’s Internet infrastructure. NoName057, People’s CyberArmy, 22C, CyberDragon, Horus Team, UserSec and PHOENIX will launch their cyber strikes against the Swedish goals and will show all Russophobes how sponsoring Bandera’s supporters can come back to haunt you,” read the announcement.
The group has also been linked to other attacks on pro-Ukraine countries on the Ukraine-Russia conflict.
ON the same day, NoName057 also announced attacks on Riksgälden, (Swedish National Debt Office), and ISP (Inspectorate of Strategic Products).
The group also took credit for attacks on the Technical Directorate of Communications of the Capital of Prague, and the Polish mPay, an app for paying for Poland’s toll roads and Polish Public Services.
Finansinspektionen, the Swedish financial supervisory authority, also claimed to bad been attacked by an overload attack.
Hack hit 120 government agencies
The largest attack so far this year was on a data center of the Finnish software and service company Tietoevry Corporation on January 19-20.
The ransomware attack was made by the Russian-linked hacker group Akira. Tietoevry said it was able to stop the attack and confine the impact to one platform.
Numerous organizations, including 120 government agencies, 23 municipalities and regions, and 35 companies were affected by the attack, with many facing various problems for days. One issue included Sweden’s largest HR system which had to be shut down entirely.
“Russian hackers have teamed up again and this time decided to bring down Sweden’s Internet infrastructure.”
Hackergroup NoName057
Kimmo Alkio, CEO of Tietoevry, said: “Ransomware attack creates severe situations, and we have taken this highly seriously from the beginning at Tietoevry, continuing to work on high alert and putting all our efforts to support our customers with the remaining recovery steps.”
Some chain stores also reported having their websites go down, and one even had some of its physical stores shut.

Photo: Kristian Pohl/Government Offices of Sweden
Filmstaden, Sweden’s largest cinema chain, had problems with its paying and booking system – customers could only pay in-house with the mobile payment app Swish.
For Vellinge municipality, the attack on Tietoevry resulted in the loss of many patient journals, which couldn’t be recovered. “This is very serious. A lot of data was encrypted during the attack and we see it as lost data,” Gustaf Lorentz, head of communication in Vellinge municipality said. He had seen no signs of personal data being leaked.
After the attack, a total of 178 incidents of suspected personal data breaches were reported to the Swedish Data Protection Agency. At a press conference, Civil Defence Minister Carl-Oskar Bohlin emphasized the seriousness of the attack and voiced concern that it could be one of the most serious challenges the country has ever faced.
Before the big attack on Tietoevry’s data center, Jämtlands County Fire and Rescue Service also had an attack on its IT-system – which, luckily did not affect the operational side of rescue and fire events.
Ransomware attacks
Elsewhere, Bjuv’s municipality was hacked in a ransomware attack – the hackers threatened to leak stolen information such as secret documents, contracts, and personal files on the Darknet.
Bjuv’s municipality said it did not know what documents the hackers had gotten hold of.
Mediplast, a supplier of medical technology products, was also attacked by the 8Base ransomware group. Hackers are said to have stolen invoices, receipts, accounting documents, personal data, certificates, employment contracts, confidentiality agreements, personal files, and more. The ransom date has been set to March 13.
The attack on Mediplast also affected a large number of the company’s customers, and made the four regions – Västerbotten, Sörmland, Blekinge and Uppsala – activate crisis management protocols.